Learning Cryptography Through Analyzing Ransomware: Jigsaw and Turkstatik
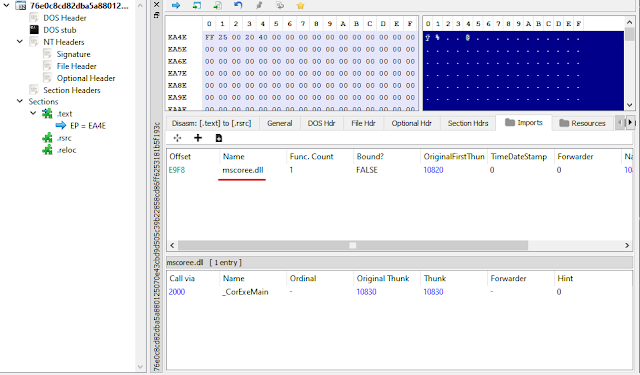
In the malware family, ransomware is like a flashy cousin who gets all the attention. The immediate impact and psychological terror of ransomware bring it an incredible amount of recognition and visibility. Today we will take a look at 2 ransomware: Jigsaw and TurkStatik 1. Jigsaw Sample : 76e0c8cd82dba5a880125070e43cbd9d505c39b22858cd86ff6253181b5f193c From looking as the Import, Jigsaw appears to be a .Net application which is great news. Instead of IDA, you can use any commercial .Net decompilers to get the accurate C# codes. I highly recommend dnSpy . It's FREE while also having debugging functionality. Opened in dnSpy, this sample is unpacked and non-obfuscated. First. we start our analysis by looking at the Resources section There are 3 pieces of information stored here: an array of "supported" extensions, the JigsawImage , and the crypto wallet address. Next, we move on to the code section inside each module. Conveniently, Main...
