Breaking Down A Variant of GlobeImposter Ransomware
GlobeImposter Analysis
Sample: 28f7aeea9a0a1f79f792213f44475e9d5d9304cd0e61e3ecb2b9d38e0271a310
This GlobeImposter sample is unpacked, non-obfuscated. All the APIs are linked in load-times, so the IAT is reliable. If you are new to reverse C++, this is a great beginner tutorial.
Starting point
For this sample, I started the analysis by running the FindCrypt-Yara plugin. The corresponding result includes references to a Base64 table and a Prime_Constant used in RSA cipher. Tracing Base64 table references will lead you in the middle of id (public key) encryption routine at 0x40E880 which we will in-depth later. On the contrary, if your starting point is pivoting CreateProcessW or ShellExecuteExW, you will get to the main function at 0x40FFF0
Drop Files
The GlobeImposter malicious behavior starts with calling the function at 0x410830 is to drop 2 files: ids.txt in the current process directory and HOW_TO_BACK_YOUR_FILES.exe in every directory that the ransomware traverses. The ids.txt includes the Base64 encryption of the public key which is used for file encryption. Interestingly, the key data is also added to the end of all encrypted files. The ids.txt file is also used for error logging.
The binary of the HOW_TO file is embedded unencrypted in the data section at 0x429390. It is used to display the ransom notes by generating a full-screen window that the victim can't close through GUI (Alt + TAB works). Even though this file is written to disk early, it's only executed after the ransomware finishes the file encryption routine.
Environment Preparation
After the file dropping, the ransomware moves on to setting up the environment by turning off security features. First, the function at 0x4105A0 is called to disable the following Windows Policy:
HKEY_LOCAL_MACHINE (hKey: 80000002h):
- SOFTWARE\Policies\Microsoft\Windows\HomeGroup
- DisableHomeGroup
- SOFTWARE\Policies\Microsoft\Windows Defender
- DisableAntiSpyware
- SOFTWARE\Policies\Microsoft\Windows Defender\PolicyManager
- SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection
- DisableBehaviorMonitoring
- DisableRealtimeMonitoring
- DisableOnAccessProtection
Next, the function at 0x4106A0 switches off WindowsUpdateCheck and set up persistence using the RunOnce registry key. After registry modification, the ransomware moves on to execute the following commands at 0x410250
@echo off vssadmin delete shadows /all /quiet sc config browser sc config browser start=enabled sc stop vss sc config vss start=disabled sc stop MongoDB sc config MongoDB start=disabled sc stop SQLWriter sc config SQLWriter start=disabled sc stop MSSQLServerOLAPService sc config MSSQLServerOLAPService start=disabled sc stop MSSQLSERVER sc config MSSQLSERVER start=disabled sc stop MSSQL$SQLEXPRESS sc config MSSQL$SQLEXPRESS start=disabled sc stop ReportServer sc config ReportServer start=disabled sc stop OracleServiceORCL sc config OracleServiceORCL start=disabled sc stop OracleDBConsoleorcl sc config OracleDBConsoleorcl start=disabled sc stop OracleMTSRecoveryService sc config OracleMTSRecoveryService start=disabled sc stop OracleVssWriterORCL sc config OracleVssWriterORCL start=disabled sc stop MySQL sc config MySQL start=disabled
Near the end, when all the victim's files are encrypted, the following script is also executed to delete shadow copy and backup:
@echo off vssadmin Delete Shadows /all /quiet reg delete "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Default" /va /f reg delete "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers" /f reg add "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers" for /F "tokens=*" %1 in ('wevtutil.exe el') DO wevtutil cl "%1"
Multi-Threaded File Encryption Mechanics
The dispatcher function is in charge of leaving the HOW_TO file in each directory that the ransomware traverses. It uses the combo of FindFirstFileW + FindNextFileW to search for each file in the directory. Then, the file extension is checked against the predefined supported extensions at 0x4290A8 (too long to include) and the whitelist below:
- Bypassed files: "windows", "bootmgr", "temp", "pagefile.sys", "boot", "ids.txt", "ntuser.dat", "perflogs", "MSBuild"
- Bypassed extensions: ".dll", ".lnk", ".ini", ".sys"
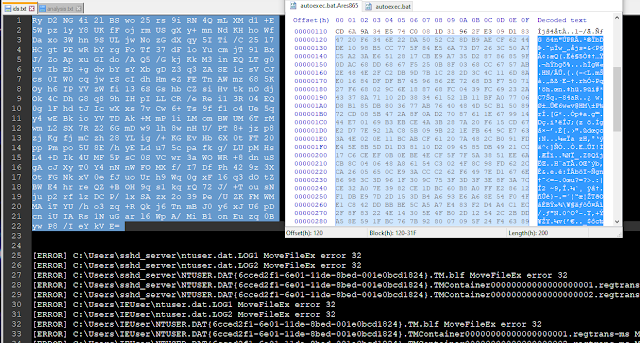
Finally, SetFileAttributesW is called to make sure each file is modifiable before being passed to file_encryption_routine(). The function starts by replacing the original file with an identical but larger in size (via MoveFileExW). An extension of ".Ares865" is added to the filename as well. Next, the key is copied to the end of the file before the original data is replaced with the encrypted one (via CreateFileMappingW + MapViewOfFile).
Cipher Analysis
From the dynamic analysis, GlobeImposter produces different public key each run. Since the ransomware shows no behavior of sending any info over the network, I suspect there are 2 ciphers being used. First, a key is randomly generated to encrypt the files. Then that key is encrypted by a predefined public key. The encrypted key is embedded into each file, in which the threat actor can decrypt through his/her private key and recover the file when the victim has paid.
Since the malware carries its own cryptography algorithms (static linking), I am having a little problem reversing them. I promise to finish this in the near future



Comments
Post a Comment